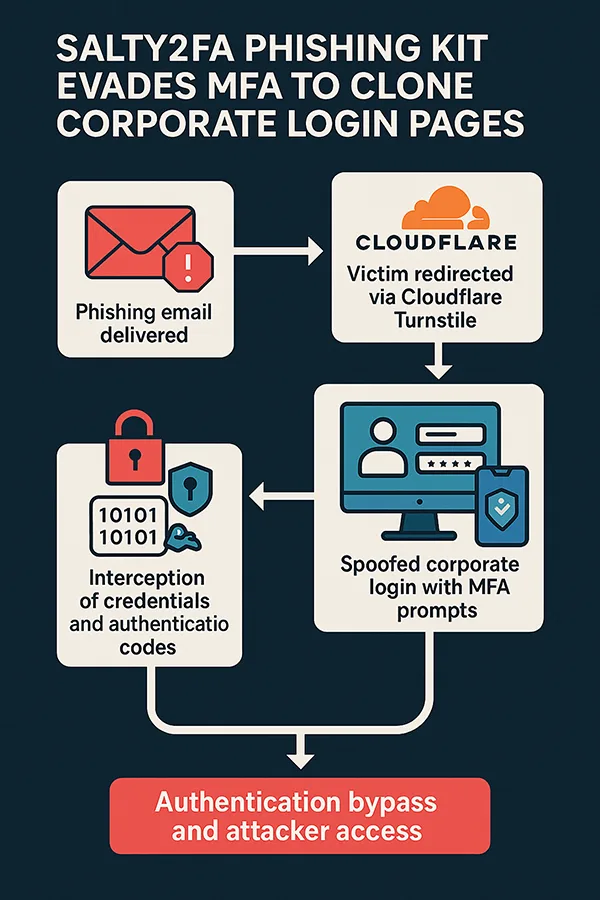
A new phishing-as-a-service (PhaaS) toolkit called Salty2FA has been discovered, capable of completely bypassing multi-factor authentication on Microsoft 365 and other corporate platforms. The kit uses multi-stage clones of login portals and sophisticated spoofing techniques—including push notifications, SMS, voice, and app-based 2FA—to harvest access credentials.
Salty2FA employs advanced evasion tactics such as Cloudflare Turnstile filtering, dynamic domain infrastructure combining .com subdomains and .ru domains, obfuscated JavaScript, and anti-sandbox logic to elude detection. Researchers note its rapid rise since mid-2025 and widespread impact across multiple sectors and geographies.
Why It Matters
Salty2FA represents a pivotal leap in phishing capabilities—undermining trust in MFA, long considered a strong line of defense. Its ability to mimic legitimate systems and intercept authentication codes in real time forces companies to rethink authentication strategies and embrace behavior-based threat detection.
Key Takeaways
- Salty2FA is a phishing kit designed to bypass SMS, app, voice, and push-based MFA.
- Uses Cloudflare Turnstile, obfuscation, and dynamic
.com/.rudomain pairings to evade detection. - Spoofs login portals with credible look and feel to harvest credentials and 2FA codes.
- Targets Microsoft 365 and enterprise users across US, EU, and other sectors.
- Behavioral detection, sandbox analysis, and phishing-resistant authentication are key defenses.
Source: HackRead (reporting by Deeba Ahmed)